In the last blog post we learned out to encrypt and decrypt secret messages to send our friends using a Shift Cipher — However, in order to decrypt we need to know they key (i.e. the # to shift the alphabet by). In this blog post we are going to learn how to crack the code if we see an encrypted shift cipher message without knowing what the shift # is, and also how to crack it if we have SOME information about the message.
Trying All Possible Keys
One of the many and most obvious ways to crack the code is to use something called the Brute Force method — In other words, to try every single possible key and see if it gives us a readable message. This would be insane to do by hand, but that’s where coding comes in handy!
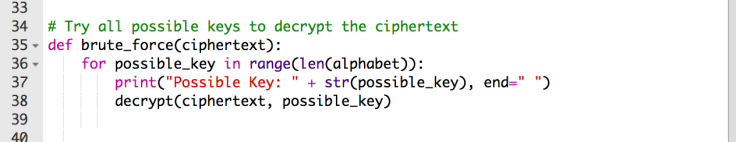
We are going to start by opening our python file from the previous blog post. At the very bottom, we are going to create a new method and call it brute_force. Since the only information we have is the encrypted message, this method will only take the cipher text as an argument.
def brute_force(ciphertext):
Inside this method, we want to cycle through a range that is the same length of the alphabet variable list that we created earlier to look for the possible key. We can use a for ____ in range(____) loop for this, using len() (stands for length). I then want it to print out every possible key (telling me what the shift number is) and then use that key to decrypt the message. This way, I can find the message that makes the most sense!
Let’s test this out! Below I have an encrypted message that we don’t know the shift # for.
SE JOGXE OY OT ZNK YKIUTJ JXGCKX UL SE JXKYYKX
Let’s go ahead and call our brute_force method, giving it the argument of that secret message
brute_force(‘SE JOGXE OY OT ZNK YKIUTJ JXGCKX UL SE JXKYYKX’)
You should now see 25 different keys that were used to decrypt the message. Reading through the list, there is only one that makes any sense

Through brute force and trying every possible key, we were able to find out that the key was 6, and the message was “my diary is in the second drawer of my dresser” (information that I certainly did not want people knowing, hence why it was encrypted!).
Brute Force With Some Information
In some cases, we might know a little bit of context behind what the secret message could be about. For example, if my brother got ahold of this encrypted message, he might have a feeling that the message was about the whereabouts of my secret diary. Knowing this, we can use the brute_force method and refine it even further by including known information or words that might be in the message.
To do this, let’s create another method and call it brute_force_known_content — Needing the ciphertext and the known_content
def brute_force_known_content(ciphertext, known_content):
Just like in our brute_force method above, we are going to want to create another for loop to loop through every possible key in our alphabet. We’ll also want to create a new variable called possible_plaintext and give it a value of an empty string. For every character in the ciphertext, we want to do the checks that we did in the previous blogpost: If the letter is capitalized, then we want to switch it to lowercase, we are going to want to index (get the position) of every character in the alphabet variable, create a new_index that checks the letter’s position, subtracted the possible key that we are testing, and then making a new variable called plain_char, which will the alphabet’s new_index.
Instead of breaking this down, I want you to give this a try on your own referencing the code the we did from the previous blogpost. If you get stuck, I have the code below 🙂
Don’t forget to add an else to your if, for any characters that are not letters to be left alone (i.e. spaces)!
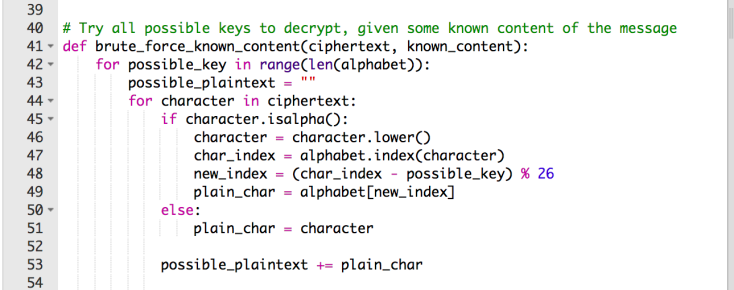
We aren’t quite done yet! The last bit that we need to add is a print. However, since I know a little bit of the content this time around, I don’t need to have it print every single possible key. Instead, I only want it to print the possible keys where the decrypted message has that known content in it (In this example, the word “diary”). Inside our possible_key for loop (but NOT inside the character for loop!) let’s create an If statement for when that known_content is in the possible_plaintext. If it is, I want it to print what the key is and also the possible message!
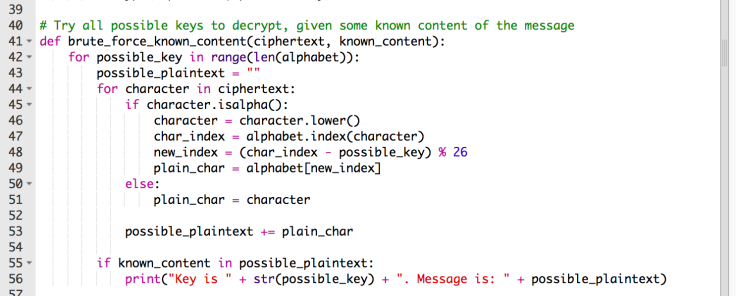
That should be it — Try it out by calling our method, and feeding it the encrypted message along with the known word.
brute_force_known_content(‘SE JOGXE OY OT ZNK YKIUTJ JXGCKX UL SE JXKYYKX’, ‘diary’)
This time around, you should only be getting the possible solution using the diary!

Summary
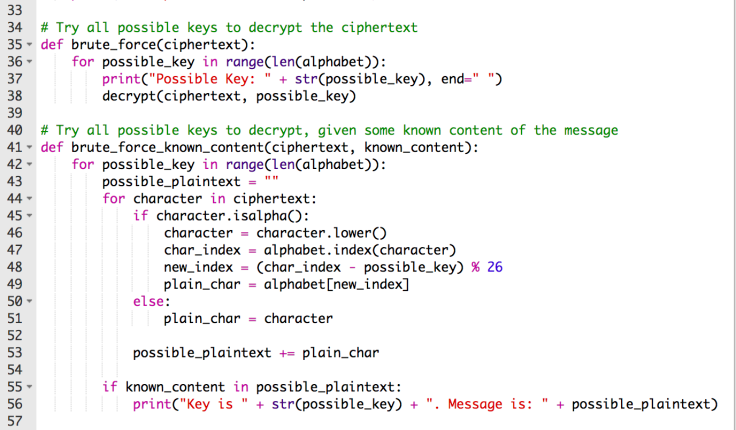
You should now able to encrypt and decrypt secret messages, along with being able to crack Shift Cipher messages using code! If you run into any bugs or errors that you cannot figure out, feel free to leave a comment below with your code and I can take a look. Just in case you need it, below is a screenshot of the full code from this blog post.

Leave a comment